This is the accompanying blogpost to the Magnet User Summit 2022 talk: [Air]Tag You're It!
Bluetooth Low Energy and You
First, a primer on Bluetooth based tracking. Bluetooth Low Energy (BLE) is often used with bluetooth beacons in order to transmit location from a beacon back to a smartphone. These devices are often just a 1 way transfer, sending data back to smartphones, not reading data from them. Typically, these beacons are used by specific applications, so only that given application can track the user. These beacons can serve multiple functions, such as alerting you that you're near an Apple Store so you can make an appointment. Others might be used in museums to give you more information about an exhibit as you approach it. There are different types of BLE beacons, including Apple's own "iBeacon" used in retail stores and other locations worldwide. For more info on BLE, please refer to this article.
While beacons can have a number of varied purposes, one of their most common is that they're used as trackers for lost items. Similar to other devices such as the Tile, Chipolo, or TrackR devices, these beacons can help you locate lost items such as keys. iBeacons work by broadcasting a UUID (universally unique identifier) that can only be understood by using an online source to translate this back to a separate identifier. Apple uses this system to help maintain user privacy.
Capitalizing on this function of BLE, Apple released the AirTag devices April of 2021. These devices are similar to other BLE tracker devices, however, feature several more unique features. Most device trackers like Tile, for example, require a device to have the Tile application in order to broadcast back to these devices and alert the user where they are located. Apple's AirTags instead utilize the FindMy service and BLE so that they can communicate to virtually any smartphone in the world without the need of an application. This gives Apple a much wider mesh network for those that use the AirTags worldwide.
AirTags also utilize Apple's U1 chip to perform ultra-wideband broadcasts. These are high speed broadcasts that are designed to send a lot of data very quickly. The UWB (ultra-wideband) technology isn't extremely new, but has been used by Apple in mobile devices and AirTags since 2019. The UWB technology is used for precise item location for the AirTags which allow you to see which direction your AirTag is from you and how far away the device is.
Apple's AirTags use the FindMy service so that any devices that come within range of an AirTag will broadcast back to Apple where that beacon was seen. While this is great from a usability perspective, what happens when someone uses one of these for a more nefarious purpose? What if a user slips an AirTag (normally $29USD) into someone else's property and uses it to track them? This principle isn't new, and I have personally worked multiple cases where bluetooth tracking devices were used to stalk an individual. With Apple having a much larger network of devices than some of its other tracker counterparts and the user not needing an application to report locations, how is Apple keeping people safe from this unauthorized tracking?
The short answer, is that they're trying, but not doing the best job in the world. But more on that in a minute.
First, let's explore AirTags from a physical perspective. The devices are roughly the same size in diameter as a lid from my favorite drink of choice, Diet Coke. They feature a metal cover embossed with the Apple logo on one side and white plastic on the other. Underneath the metal cover is a CR2032 battery which powers the device which Apple states should have "more than a year" of life. Under the battery there is also some identifying information of the AirTag including the device's Serial Number. This is where the teardown ends unless you choose to get destructive. Below the cover, though, is a layered donut-shaped board.

(Image credit ifixit.com)
The chips include Apple's U1 ultra-wideband chip, a Nordic Semiconductor BLE/NFC Controller, and a NOR storage chip boasting a whopping 32Mb of storage space.
Pairing and Using AirTags
To use AirTags, Apple requires the user to have an Apple ID. The Apple ID is used so Apple can take the broadcasted information and report it back to a specific user. Once the small plastic tab is removed from the AirTag, which separates the battery and its connectors, all users have to do is bring it near their iOS device. Once there, a prompt will allow the user to start the connection and pairing process. Users can also set a custom emoji and name in addition to a set of pre-created names to help identify their devices. Setting the device's type is important because it can allow Siri to locate your device, especially if you're like me, and ask her to "Find my Keys" about 5 times a day.
During the pairing process, information, including a key pair, is exchanged with the AirTag and stored on the iOS device; it gets shared via CloudKit to other devices on the Apple ID, including shared family members. You cannot "share" an AirTag, but the identifiers do get shared automatically with other family share members. Several services track the use of AirTags within Apple's Unified Logs, including:
- locationd
- FindMy
- searchpartyd
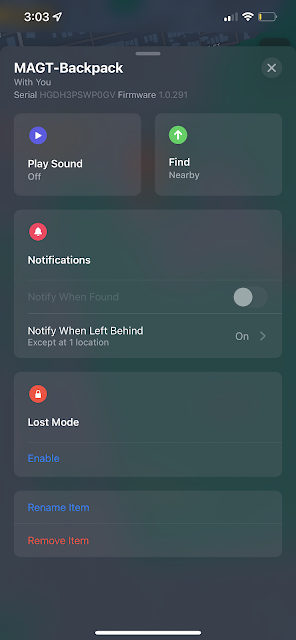
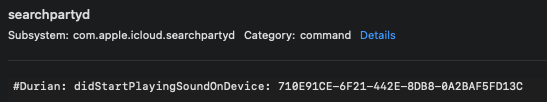
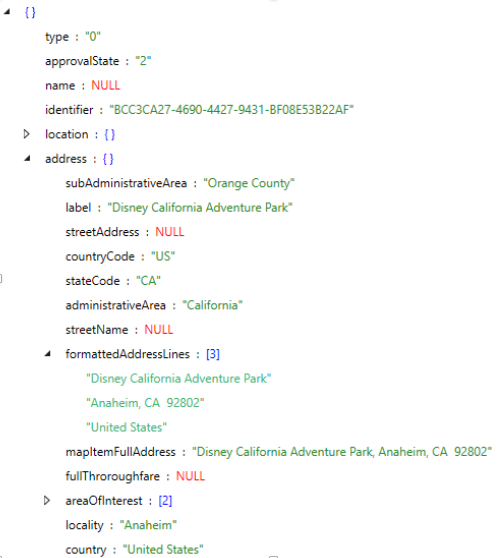
The process "searchpartyd" seems to be the most commonly used when discussing information found within the Unified Logs for AirTag devices. Once the device is paired, data such as the serial number, the provided UUID, key storage location, pairing date, and custom name can be found in the logs.
Note that the word "durian" gets used in the above screenshots. This is because durian is the device codename given to AirTags. Using that value will help you identify records relating to AirTags in the Unified Logs; however, Apple highly privatizes this information. To actually see the UUID values listed above in a sysdiagnose capture, users must first install the AirTag mobile configuration profile. The following example is from a capture of the logs using a sysdiagnose capture method without the profile being installed:
Playing Sounds and Locating Devices:
When the user tries to locate the device, because of the UWB connection, a large number of logs will be generated while the proximity location is being triggered.
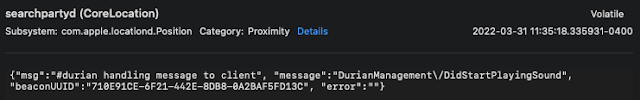
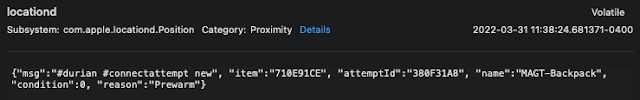
"Protecting" Users with Randomization
As seen above, when an owned AirTag is broadcasting with a device either owned by that same user or one in their family share plan, it will use the UUID value. This value seems to stay static in these situations. However, if the AirTag is not already trusted with that device, the broadcast UUID is actually randomized. While this would be okay if it at least remained static, the UUID actually randomizes and changes multiple times each day. I saw an AirTag change its broadcast UUID to unauthorized devices numerous times each day in my testing.
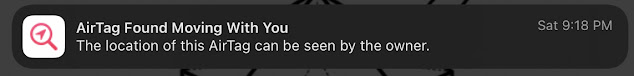
While that is happening in the internal logs of the device, what is happening that the user can see? Once an unauthorized AirTag (or compatible FindMy accessory) has been seen traveling with the iOS/macOS device owner for a period of time, a graphical alert will display on that device. As of iOS 15.4, Apple changed this icon from the standard FindMy alert icon to a unique icon showing the difference between a device that has been left behind and an unauthorized device.
Once the alert is clicked on (which is classified as a "Time Sensitive" notification and MAY override certain Focus settings), it will open the FindMy app so that the user can see information including where the device has been seen with them as well as when it was "first" seen. This information, however, may not be completely accurate.
From my testing, the window of time is a big concern. Apple states in their limited documentation that the alert will trigger after the device has been seen with a user at a random time between "8 and 24 hours." Later versions of iOS 15 seemed to shorten this window, but Apple has not provided any official documentation on the how, when, or why this happens. From my testing I received a range of time between 1 hour and 8 hours. Apple also seems to trigger these when you reach locations they have deemed as "Significant Locations" but it also may alert at other times as well. The above screenshot is an example of one such test where the device is "first" seen with me at 0500 (even though I had it a long time before that) and it shows me traveling down the road, flying to Atlanta, and finally arriving in the Washington D.C. area. However note that the time on the phone is 1307. This was opened only minutes after I received the notification meaning that Apple took eight hours to alert me this AirTag had been traveling with me! The other issue is that Apple will alert only when the user's trusted devices are not seen near that AirTag so close range tracking may not alert as frequently.
Like before, you can see a UUID showing up and that the device is "unauthorized." Unfortunately, this UUID will NOT match what the owner of the AirTag would see (nor would it be stored on the device the same way).
Once the device has been located, all the user can do is get an NFC broadcast from the AirTag, which will open a page in the default browser. This page from found.apple.com will then display the listed serial number of this device.
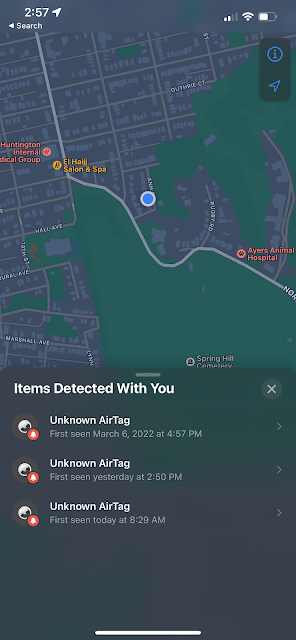
Problems with Randomization
The above screenshot shows 3 "Unknown AirTags" but it's actually the same device which has alerted 3 different times because of the UUID rotation.
How can we identify the owner with no stored artifacts on our victim device, directly tying unauthorized AirTags to the owner, and the UUID being rotated? Unfortunately, we can't do it alone. We'll need Apple's help with that. Because the records are passing back information to Apple's servers, Apple will be able to show who the owner of the AirTag is as long as it's been registered to an AppleID (which it should have been during the setup process for tracking). Apple's own Law Enforcement Guidelines state they can provide AirTag pairing history for up to 25 days with a "subpoena or greater legal process." It is unknown if Apple has a way to show how long an unauthorized device has been detected by a victim's device. Their own guidelines state, "Location services information for a device located through the Find My feature is customer-facing. Apple does not have content of maps or alerts transmitted through the service." They also state that they cannot view the location of any AirTag.
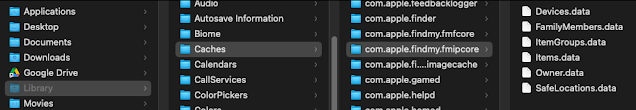
Stored AirTag (and Other) Aritfacts
- FamilyMembers
- SafeLocations
- Items
- Owner
- ItemGroups
- Devices
The Items.data file will store the listed AirTag device as well as some other Find My accessories. Third-party accessories may be divided between both the Items.data and Devices.data files. The Items.data JSON file will store for each device:
- Names
- Serial Number
- Custom Emoji
- Last Detected Location
- Last Crowd Sourced Location
The Devices.items file stores similar information to the Items.data file however it tracks other stored iOS and macOS devices that have been tied to the user's Apple ID. While the device's serial number or UDID will not be readily available, other information for both iOS and macOS devices are tracked here including:
- Model Numbers
- Names
- Address last seen
- Other status data
Conclusion:
AirTags and Apple's use of Bluetooth tracking beacons certainly aren't going anywhere. There have already been many cases where people are trying to use AirTags to stalk or follow someone else and to be honest, Apple still has some work to do to protect users. While the artifacts are great once you have a suspect device, the UUID randomization can be problematic if you only have the victim's device. While Apple does allow for information to show us the paired records between Serial Numbers and Apple IDs, it will require some legal process which is not always an option.
On the other side, once you have located a rogue AirTag, you can match it via Serial Number within the owner's macOS or iOS device. Other artifacts such as KnowledgeC or PowerLog may also show you when the Find My application was used to view this tracker (although not precisely the rogue tracker, just the service in general). The .data files can be beneficial since they store the name of the device, saved emoji, and the serial number. If the AirTag has been called something specific such as "Lisa's Car" it could potentially help to support your case.
While the transition to the new notification icon for rogue devices in 15.4 is helpful, I believe Apple still has a way to go to protect people from planted rogue devices. Just playing the sound is not enough, and precision location finding would be helpful, but Apple has still yet to implement that function. This would also require UWB equipped devices such as an iPhone 11 or higher, meaning not all devices will be able to locate it. There's also the Android problem. While Apple has released an application to allow you to sweep for AirTags, it's still a manual process, and just because one is detected doesn't mean it hasn't been with you for a long time. Apple's documentation also needs work on the when, how, and why they choose to alert users that unknown devices are with them.
As Apple continues to evolve the safety mechanisms of this technology, I know I'll keep my eye on these little AirTags. That being said, I'm a HUGE fan of them myself, and I do appreciate Apple's work to keep others from using my broadcasted UUID to track my movements. Until next time, Tag! You're it!a














ReplyDeleteGreat article! I really enjoyed reading about the features and benefits of AirTags. The information you provided was clear and concise, making it easy to understand how these devices can be used for tracking personal items. Keep up the great work in sharing insightful tech content like this!
Hi sir, very interesting reading. Could you please elaborate a bit more about this statement: "install the AirTag mobile configuration profile" ? Thanks for your time
ReplyDeleteHi. Thanks a lot for your article.
ReplyDeleteWhat is about a Samsung SmartTag? Maybe you can explain what is different from AirTag.
I mean if I have owner device of SmartTag. How I can found a serial number of SmartTag on owner device. Thank.