Recently I was trying to set up an Android device to run some testing on and I just happened to pick a Samsung this time around. I needed some sample data on it but I didn't have a lot of time to generate information. Luckily, Android has a way you can restore information from one device to another, even if that device isn't an Android.
If you happen to be transferring over to a Google Pixel phone, Android will allow you to use the USB-C adapter to connect a USB-A to Lightning cable that has an iOS device running on the other side. I thought this was a pretty slick process and will likely be checking into it more in time to see what happens on the Pixel side.
Since Samsung is one of the most popular device manufacturers it shouldn't surprise anyone that they are copying this functionality on their device line. In order to do this, Samsung has the user download the Samsung Smart Switch application which can also be found on the Google Play store. (Link) Samsung isn't alone on this, with OnePlus, LG, and 3rd party groups using this same functionality, but Samsung is the one we'll focus on today.
After grabbing my iPhone test device I plugged it into the S20 I was testing out and followed the step by step process that the device had displayed on the screen.


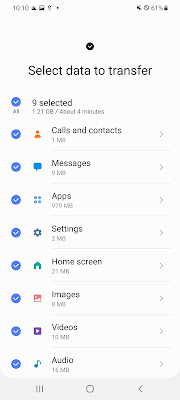
Samsung allowed me to select quite a bit of information including SMS/MMS, Contacts, Photos/Videos, and even Application data. So after this process, what is left behind by the Smart Switch application that could be relevant to our investigations?
The application uses the bundleID of com.sec.android.easyMover. Looking for that in the file system, there weren't many databases that appeared there at first. Within the shared_prefs folder, there was a "smartswitch_prefs.xml" file that had some great information in it including:
- Source Device Type
- Target Device Type
- Google Account Sign-In
Within the "files" folder of the com.sec.android.easyMover application directory, there was a LOT of interesting files left behind. First off there is a folder: data\data\com.sec.android.easyMover\files\iosotgmanagerv2\
Within this folder, a Plist file can be found identifying the source device the data came from. This is the lockdown plist file that is used as part of the Trust Pairing process of iOS.
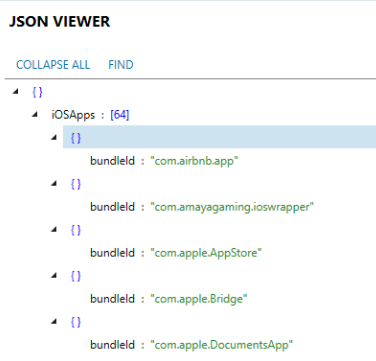
There is a folder called SmartSwitch which also has some great data. An "iosApps.json" file will store information about iOS applications detected from the source device.
A "requestedApps.json" is a JSON file keeping a log of the matching Android versions that will be requested from the Play Store as well as version.
The "BrokenRestoreInfo" directory of my device had some additional interesting JSON files. The DevInfo.json file contained UDID information, model number, OS versions, Display Name, and what was asked to be backed up.
The JobItems.JSON will let the examiner know what was able to be downloaded from the source device.
A PHOTO folder will contain additional JSON files that contain metadata about recovered photographs from the source device.
Another folder, SmartSwitchLog contains several log files about the transfer process. This folder also contains the most important piece of the application as well. In this source image, a DATA_0 folder was found containing the bulk of the transferred information. This folder contains a multitude of ZIP files that have the information backed up from the Source device. These files within the zips may be named in some cases the same SHA1-named structure as the files would be from within the original iOS device's iTunes-style backup. Several examples will be linked below:
BACKUP DATA:
DATA_0_BACKUP_INFO.zip --> Contains the Manifest.db for the iTunes-style backup which will give you a listing of every file included in a backup on the source device as well as helping to decipher the SHA1 names in the recovered files.
ALARMS:
DATA_0_ALARM_0.zip --> Contains the file cc723e4537a6d5120fb720dda7dd18b10f3f4a97 which is the Library/Preferences/com.apple.mobiletimerd.plist from the iOS device.
DATA_0_ALARM_1.zip --> Converted.xml: The converted version of the above Plist file.
BOOKMARKS
DATA_0_BOOKMARK_0.zip --> Contains the file d1f062e2da26192a6625d968274bfda8d07821e4 which is the Bookmarks.db from Safari. Also contains BookMark.xml which is the converted version of this database.
CONTACTS
DATA_0_CONTACT_0.zip --> Contains the file 31bb7ba8914766d4ba40d6dfb6113c8b614be442 which is the AddressBook.sqlitedb from the iOS device.
DATA_0_CONTACT_1.zip --> Converted VCard (.vcf) data from the above database.
MEMO / NOTES
DATA_0_MEMO_0.zip --> Contains the file ca3bc056d4da0bbf88b5fb3be254f3b7147e639c which is the notes.sqlite and the file 4f98687d8ab0d6d1a371110e6b7300f6e465bef2 which is the NoteStore.sqlite database.
DATA_0_MEMO_1.zip --> Contains a Memo.zip which has a JSON file inside it which is the converted notes data of the two above databases.
MESSAGES
DATA_0_MESSAGE_0.zip --> Contains the file 3d0d7e5fb2ce288813306e4d4636395e047a3d28 which is the sms.db from the iOS device.
DATA_0_MESSAGE_1.zip --> Contains several relevant files including:
sms_restore.json - All of the SMS messages from the above database converted into a JSON file.
mms_restore.json - All of the MMS messages from the above database converted into a JSON file.
NOTE: iMessages are organized into the appropriate JSON above for their type either SMS/MMS.
PART_files - Attachments recovered from the SMS/MMS/iMessage attachments.
PHOTOS
The PHOTO folder contains information about the photographs and videos extracted from the source iOS device, but not the media itself.
But what if you don't have a full filesystem of the device and you're stuck with just a Quick image of the data? In that case, examiners should turn to the media/0 (or emulated sdcard) directory to find the SmartSwitch directory. Within this directory under "tmp" an ENTIRE copy of the iTunes-Style backup was recovered!
Within the SmartSwitch/tmp directory there were several folders to support the transferred data. Unfortunately, not all of these kept the JSON files that were available from the data's stored information from within /data/data. Some of these folders did, such as the message_json folder containing all of the same JSON values from earlier.
The photos/videos transferred from the source iOS device were also discovered within a folder in the emulated sdcard directory called iPhoneData. This directory contained all of the recovered documents and media items transferred over. The names from the source device were not kept in this directory and the previously discussed photo logs keep the information about how the files are renamed.
Android is well known for duplicating data across multiple areas of the filesystem. If the SmartSwitch application is found on a subject's device, several directories should be checked for this previous device's transferred data. Some of these areas are more available to the end user than others so each directory may or may not still have data within it.
As a wrap up and reminder, the directories that should be checked are:
/data/data/com.sec.android.easyMover/files --> Look for the iosotgmanagerv2, SmartSwitch, and SmartSwitchLog files. Search for any DATA_0 folders for the stored .zip files containing both original source information and converted JSON data.
/data/media/0/iPhoneData --> Contains the recovered documents and media from the iOS device (original source names NOT kept).
/data/media/0/SmartSwitch/tmp --> Look for the original backup of the iOS device as well as the converted JSON data within the appropriately named folder.
And that's it for this post! In the future, I definitely want to explore the same data but for an Android to Android transfer as well as exploring the Pixel version and other manufacturer's version of the same processes.









I always prefer to read the quality content and this thing I found in you post. I am really thank full for you for this post. we also provide service for Best Smart Home Automation System india. for more info visit our website.
ReplyDelete